ALAN, CHARLIE and AMITA. Amita has her keys and purse,
looking a little stressed for some reason.
AMITA
What do you think? This time of
night, I can probably just take the
110 to the 105, right? Shouldn't
be too much traffic...
CHARLIE
If you want, we can run a quick
aggregated speed density function,
or we could do a mesoscopic traffic
simulation...
ALAN
Give the abacus a break, for once.
The Dodgers are in Houston. Rush
hour's long over. The 110 to the
105 should be just fine.
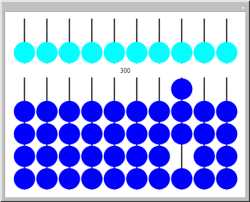
An
abacus computes numbers by sliding beads on
rods. In this Demonstration, click a bead to move it. The upper disks add 5. Thus each row can store the
digits between 0 and 9.
Hunter's iPod is hooked to Charlie's laptop, the display also
seen on one of the LCD's. Data code spills down as it did in
Don's Suburban. Charlie types as Don and DAVID look on --
CHARLIE
The encryption code is somewhat
elementary... There.
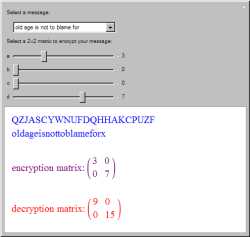
In a Hill cipher encryption, the
plaintext
message is broken up into blocks of length
n according to the
m ×
n matrix chosen. Each block of plaintext letters is
then converted into a
vector of numbers and is
dotted with the matrix. The results are then
converted back to letters and the
ciphertext
message is produced.
AUDIENCE VISION - starting very tight on only a few letters,
then WIDENING to include several words.
CHARLIE (cont'd)
It's made up of individual letters
and words, but comparing letters
and words would be meaningless...
WIDER now to include sentences and paragraphs.
CHARLIE (cont'd)
To detect plagiarism, you'd need to
look at larger strings: sentences,
paragraphs, entire pages...
Pages of the book begin to turn, more and more rapidly. A
SECOND BOOK appears alongside, pages turning in unison.
CHARLIE (cont'd)
A String Metric allows you to
compare the two systems... and
expose the plagiarist.
The page-turning suddenly stops, several passages in each
book HIGHLIGHTED. Identical.
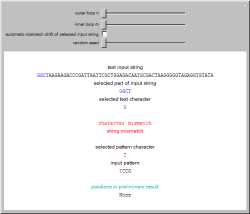
Brute-force string matching compares a given pattern with all substrings of a given text. Those comparisons between
substring and pattern proceed character by character unless a mismatch is found. Whenever a mismatch is found, the
remaining character comparisons for that substring are dropped and the next substring can be selected immediately.
Don and Colby at Don's desk, Charlie appears with the iPod.
CHARLIE
We may want to think our tastes are
unique... but they're not.
(then)
There are particular rhythms, key
changes, or chord patterns that, as
humans, we find pleasing. Just as
there are odors we find pleasant or
not...
(then)
This program's sampled thousands of
hit songs, analyzed what they have
in common... From there it can
make a fairly accurate statistical
guess as to what will be a hit and
what won't.

The aesthetic success of all music lies in the constant unfolding of novelty versus familiarity. Is the next moment
refreshingly surprising, but not too unexpected? A common compositional device that guarantees such success is to play
an existing theme backwards (retrograde) or upside down (inversion).




